“Ask this from the person who has private stuff”: Privacy Perceptions, Behaviors and Beliefs Beyond W.E.I.R.D
the big question?
How is privacy enacted and what strategies are employed by low-literate men and women to navigate the norms and perform privacy?
the goal
Understand privacy perceptions and practices among low-literate, low-income Pakistani users.
Explore the impact of cultural expectations arising from a patriarchal context on privacy beliefs.
Facilitate privacy preservation amongst low-literate low-income users given the cultural restrictions.
Understanding the existing landscape before stepping into the field
Stepping into the field
We conducted 40 semi-structured interviews (23 female, 17 male) with participants belonging to the low-literate low-income community.
Matching bandwidth with the participants
Punjabi and Urdu (local languages) as interview languages
Primary language: Urdu, as it is the national language of Pakistan.
Language flexibility: We adapted to Punjabi, the regional language of Punjab, if:
Participants responded in Punjabi.
Participants seemed to struggle with Urdu.
This approach ensured participants were comfortable and could communicate clearly during the interviews.
Interview location: A school in the participants' local area.
Provided a familiar and secure environment for participants.
Maintained a good distance from their homes to encourage honest and open responses, minimizing any hesitation they might have felt in a more personal setting.
Initial approach:
Both my co-researcher (male) and I (female) conducted interviews together.
One person focused on the interview, while the other took notes.
Observation after first 4 interviews (2 male, 2 female):
The presence of other genders noticeably restricted participants' responses.
Revised approach:
I (female) conducted interviews with female participants.
My co-researcher (male) conducted interviews with male participants.
This adjustment improved the openness and quality of participant responses.
~ female participants hesitated to mention things such as intimate health etc. in front of my male co-researcher and male participants hesitated to express their views in front of me.
Real-time reframing of the interview protocol
Making the interview protocol non-scandalous and culturally sensitive
Goal
Understand if participants were employing any privacy-preserving measures on shared phones to guard their messages, search history, etc.
Problem
Female participants were reluctant to mention that they hid something on their phones from their husbands
Resolution
I modified the interview protocol in real-time to ask them if they hid something on their phones from their children; this gave me insights into if they knew how to use a certain hiding feature or not.
Resorting to simpler terms: read receipts to blue ticks
Goal
Assess participants' understanding of WhatsApp features, specifically regarding privacy settings like read receipts.
Problem
Participants had low literacy levels and struggled to comprehend terms such as "read receipts," which led to confusion when I inquired if they had enabled that feature.
Resolution
I adjusted my interview approach in real-time by simplifying the terminology, rephrasing questions to specify "the first delete option" and "the delete option below it," which helped clarify the features and gather accurate insights.
Transition to a visual interview protocol
Goal
Evaluate participants' awareness and usage of specific app features during the interviews.
Problem
Participants struggled to understand my verbal references to certain app features, making it difficult to gauge their familiarity and usage.
Resolution
I adapted my interview technique by demonstrating the features directly on my phone, asking participants to point out the options they recognized, which facilitated clearer communication and more accurate responses.
Data Analysis
After each interview session, we dumped our insights in the form of sticky notes. At this point, the most random and unstructured insights were also drafted to ensure we did not miss out on any data and thoughts we had during interviews. We grouped these insights into sections. The sections were labeled according to whatever name we saw fit at that time.
We then refined and relabelled the insights in order to analyze them better.
Swapping roles for thematic analysis to ensure unbiased analysis
Findings
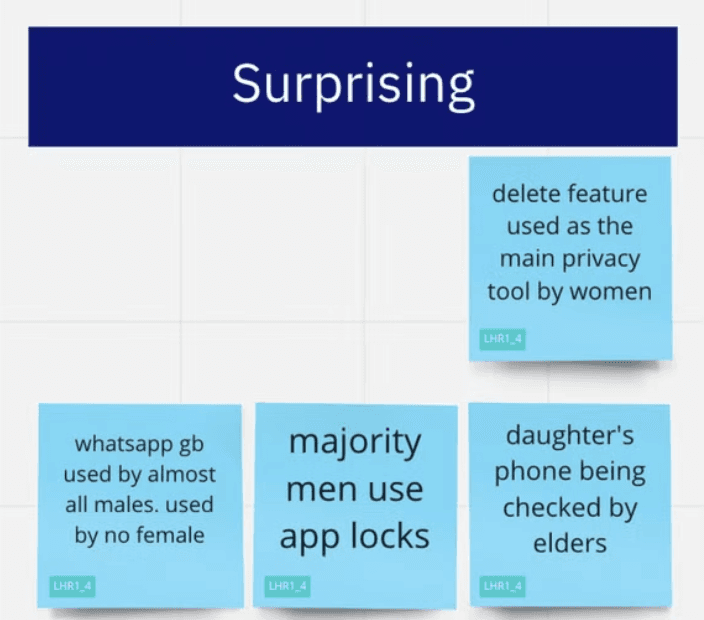
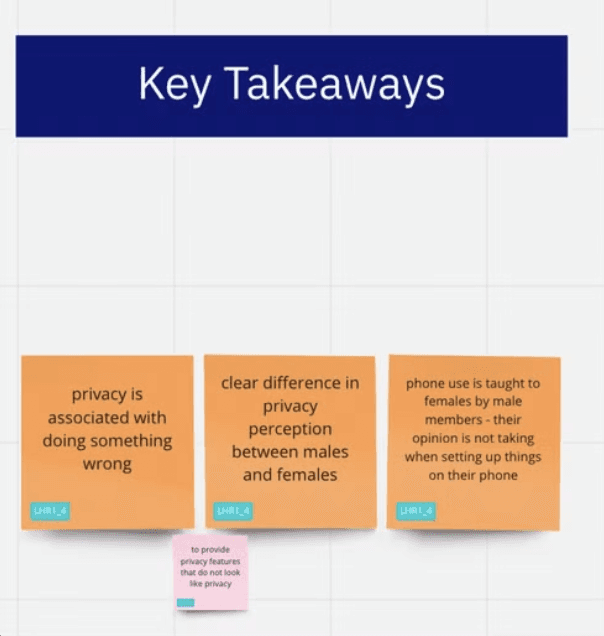
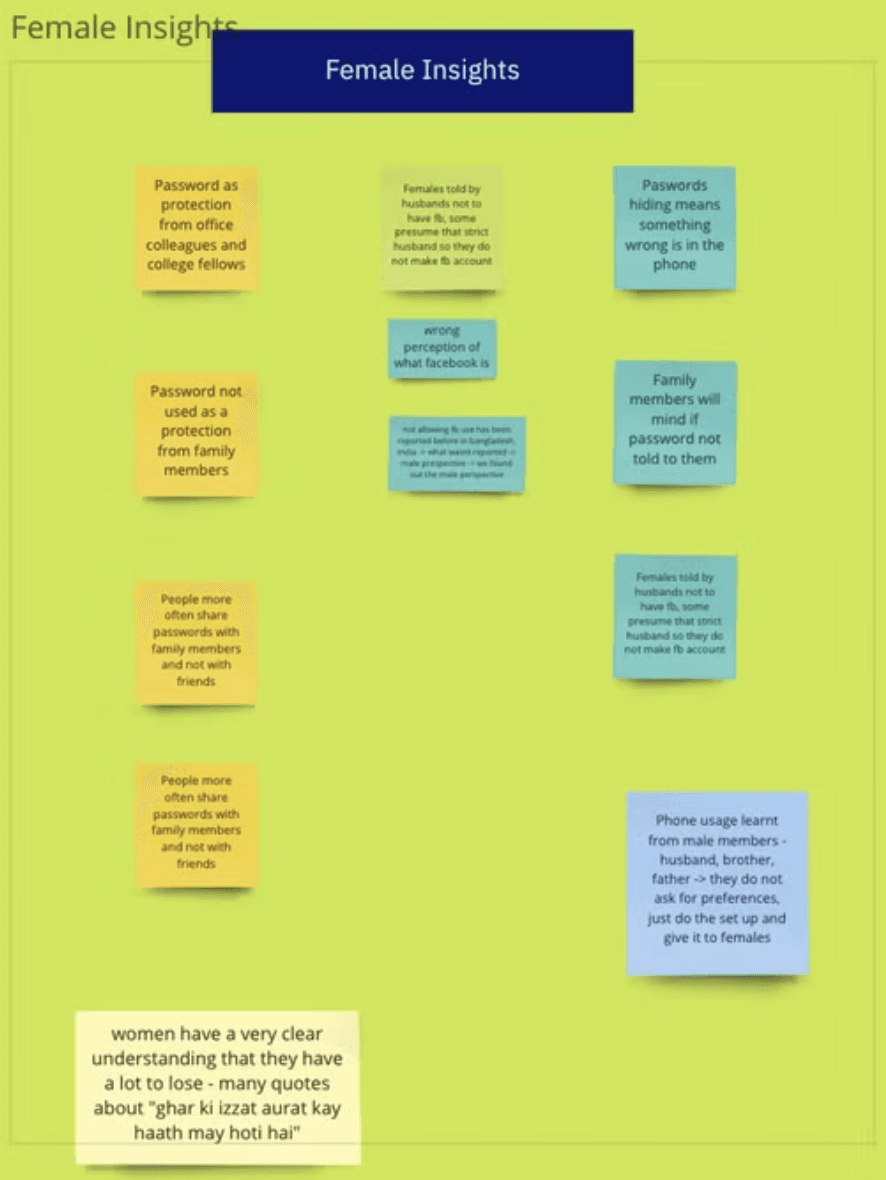
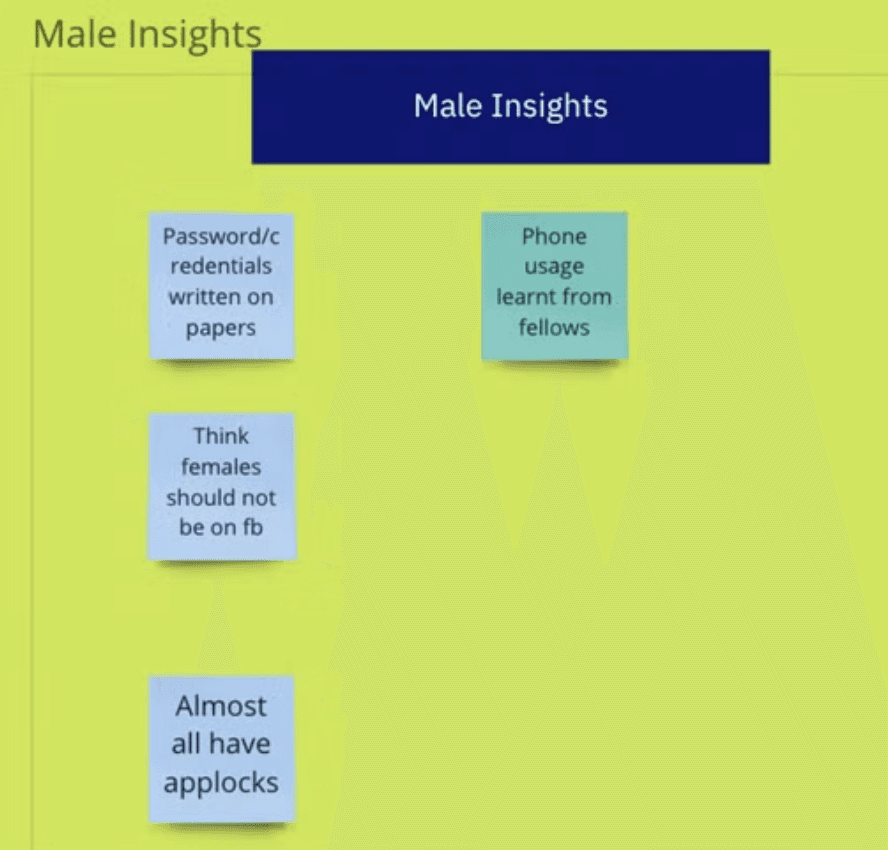
Enacting Privacy as Scandal for Women
~ " i think when you have done something mysterious or wrong only then you will feel the need to hide it from your family members. My kids are very good and my husband and I have nothing to hide from one another. We have everything in the open"
~ " i do not need a phone lock and i never will"
this leads to 2 user needs
the desire to have closed conversations about sensitive topics without the fear of some one else accessing them
traces being left behind of private conversations and the inability to remove these traces.
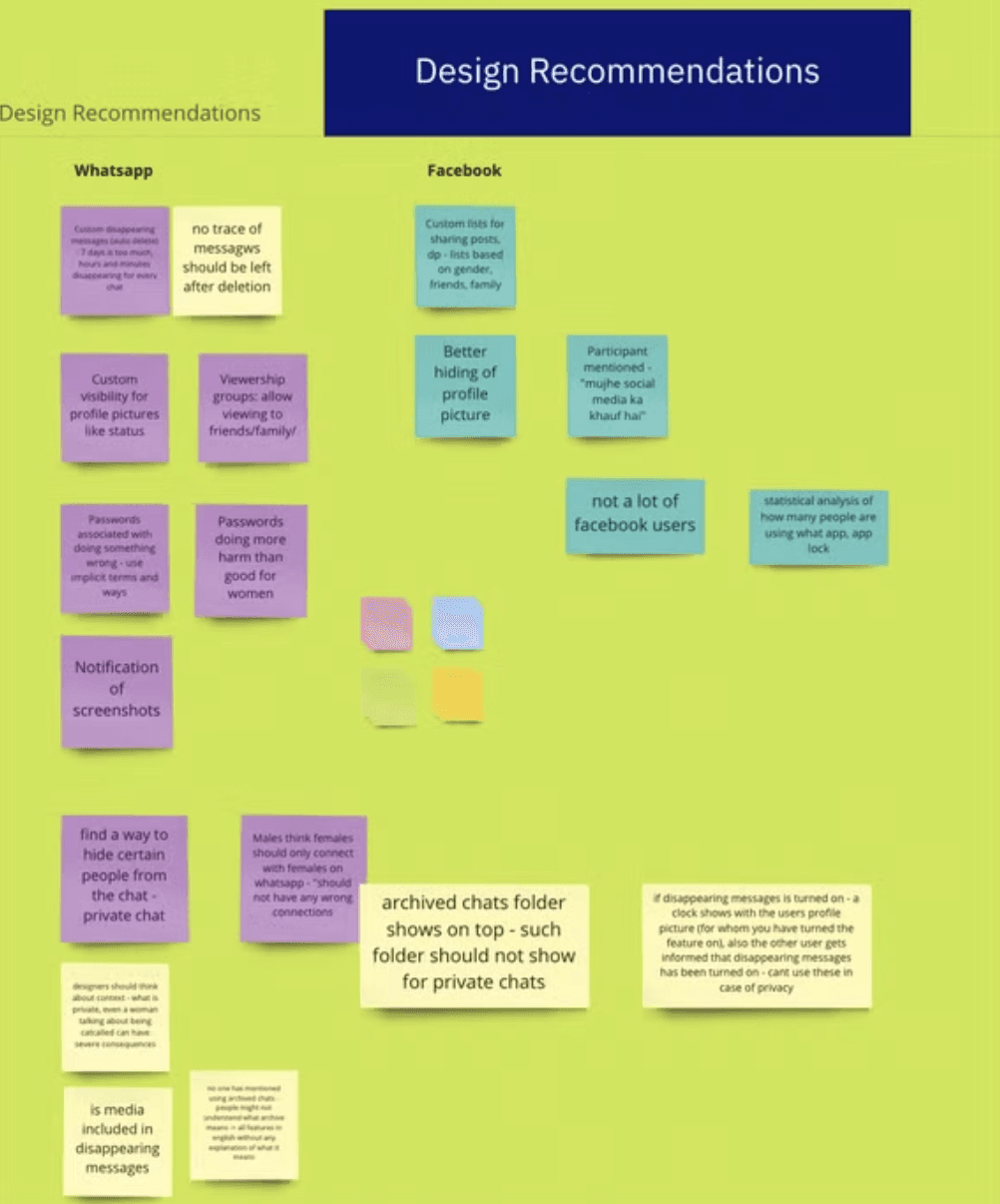
design recommendation:
Private Conversation Mode
No trace of conversations or media left on the device.
Content shared is restricted to the session only.
Interactions are organized into sessions.
Messages and media are inaccessible outside the session after it ends.
No session log is maintained.
Once the session is closed, users cannot access the previous conversation.
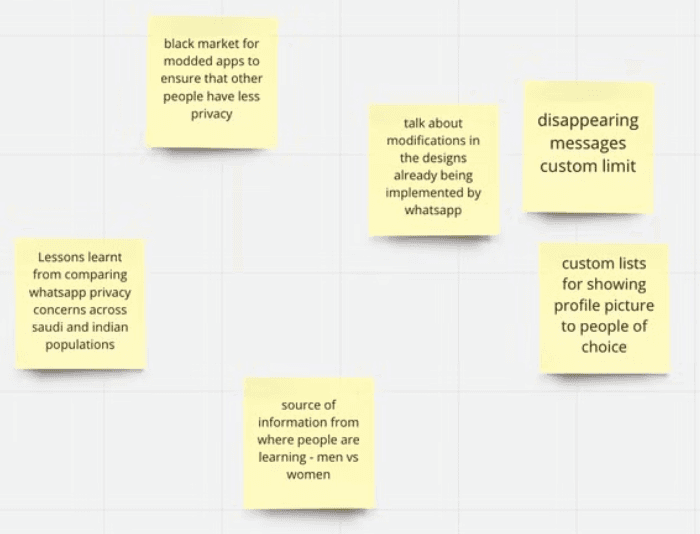
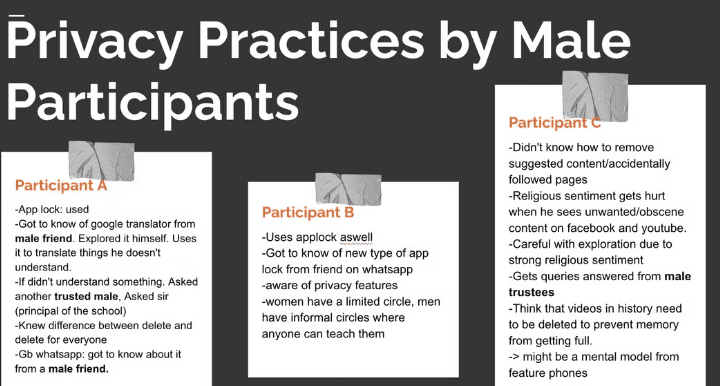
Aftermarket applications are a threat to privacy
~ " there is a sort of privacy where even when you see their story (referring to WhatsApp status) they don’t get to know about it (referring to GB and FM WhatsApp). Similarly status can be hidden from specific people as well"
this leads to 2 challenges
Users may unknowingly share information they believe they can later delete for everyone.
GB or FM WhatsApp users might view their content, such as WhatsApp Status, without their knowledge.
design recommendation:
Notification for modded apps
Users should be notified if a contact is using a modified version of WhatsApp.
User should get the option to agree or refuse to continue conversation with the person using modded app.
How did i grow as a researcher?
Culturally and Contextually Sensitive Research Questions
I learned to craft research questions that are sensitive to cultural nuances and contextual factors as one question style does not fit all.
Real-Time Protocol Adjustments
I honed the skill of modifying interview protocols dynamically to encourage candid responses, particularly on sensitive topics. This flexibility allowed me to uncover insights that participants might otherwise have been hesitant to share.
Dumping raw insights
Dumping raw insights immediately after interviews proved invaluable. It facilitated the synthesis of concrete findings later on, guiding the development of actionable recommendations.
What would i do differently?
Using a different tool for thematic analysis
I found that using Deedoose for thematic analysis posed challenges and impacted efficiency. In the future, I would opt for more user-friendly and efficient tools to streamline the analysis process.
Do more focused interviews
I would conduct more interviews but with a narrower focus . Each individual set of interviews would be about particular topic - modded apps, WhatsApp
Maintain a process book
While I do have all the materials of the project in a dedicated Google Drive folder, I would like to maintain a process book in Notion or a similar tool that details every part of the process - this would serve as a one stop for anything related to the project arranged in a chronological order.
What would i do with the results?
Discuss implementation feasibility with product teams
While we do have the results in the form of actionable design recommendations, I would want to discuss the feasibility of their implementation with the product teams at WhatsApp and see if they can be implemented
Do usability testing with the prototypes
I would make prototypes of the design recommendations and test them with the same population to further validate the findings.
Participatory design
Alternatively, I would take the results back to this population and design solutions with them.